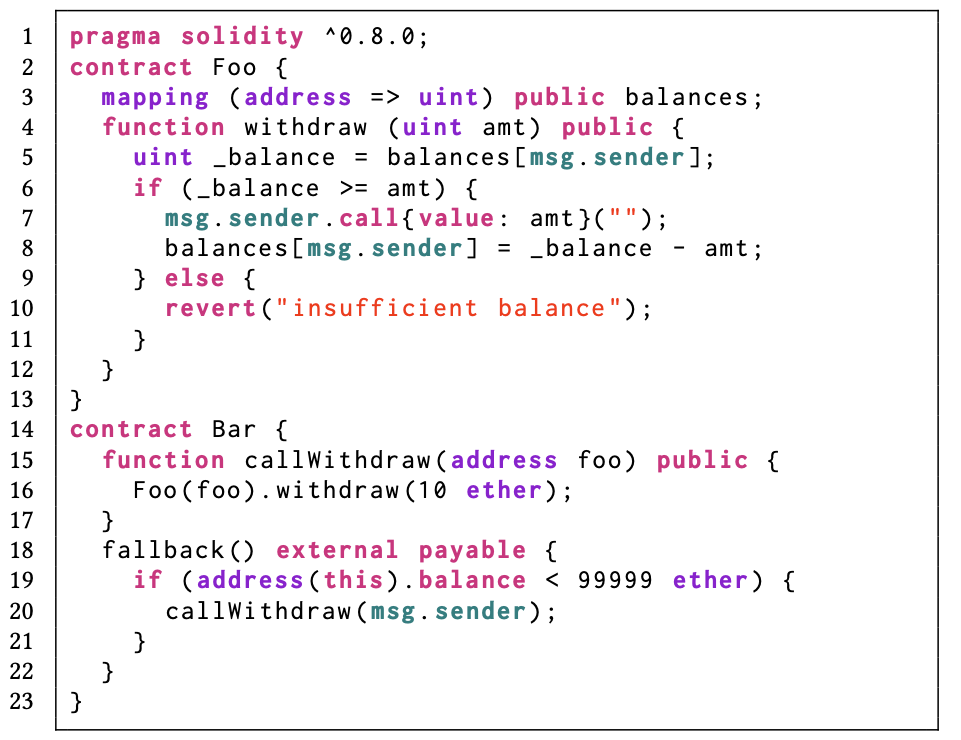
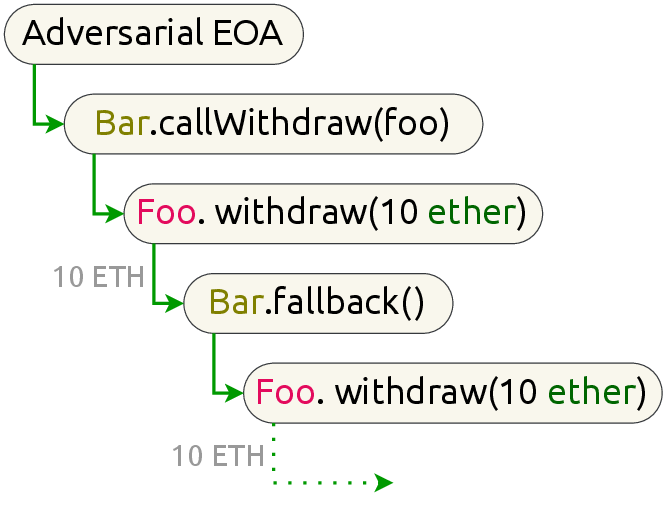
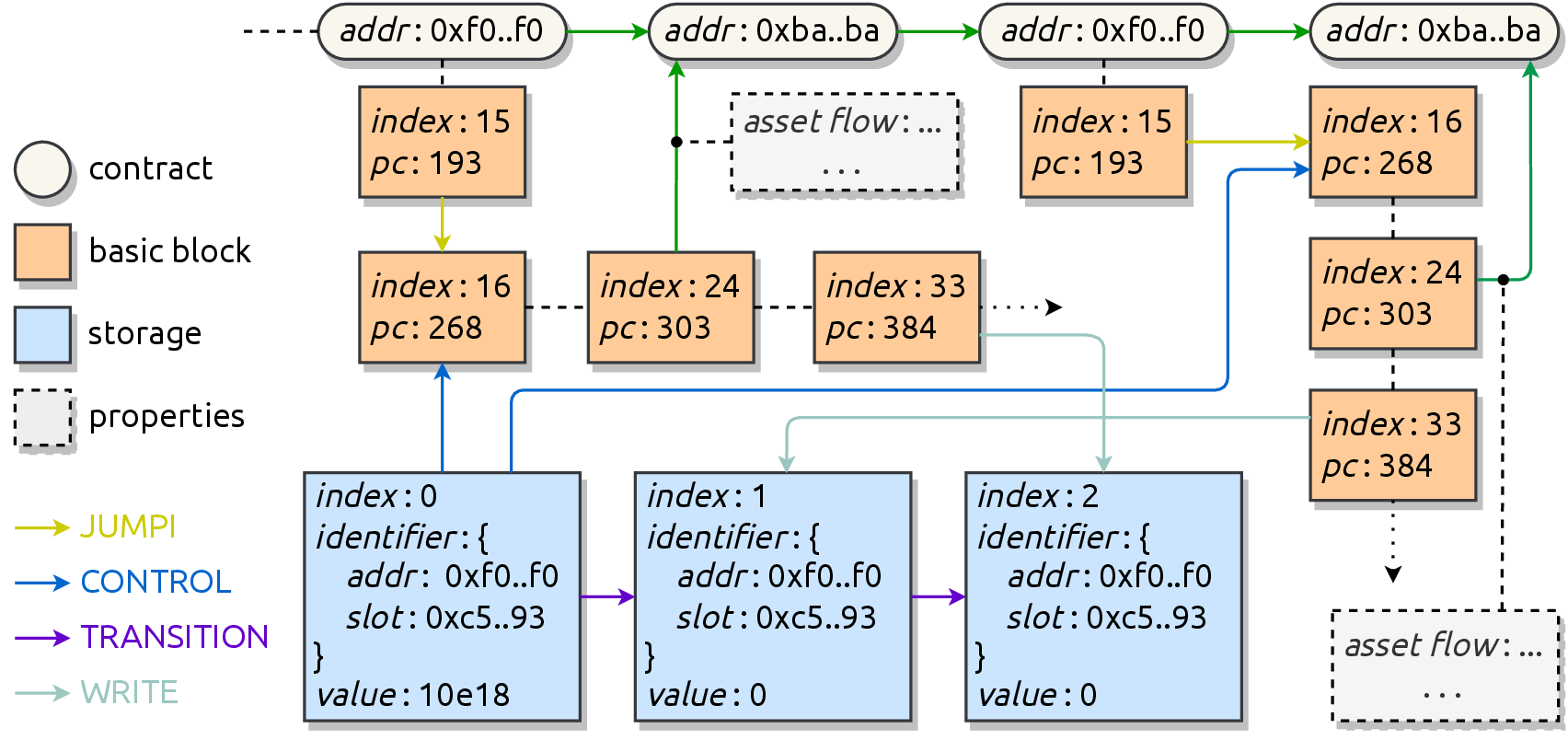
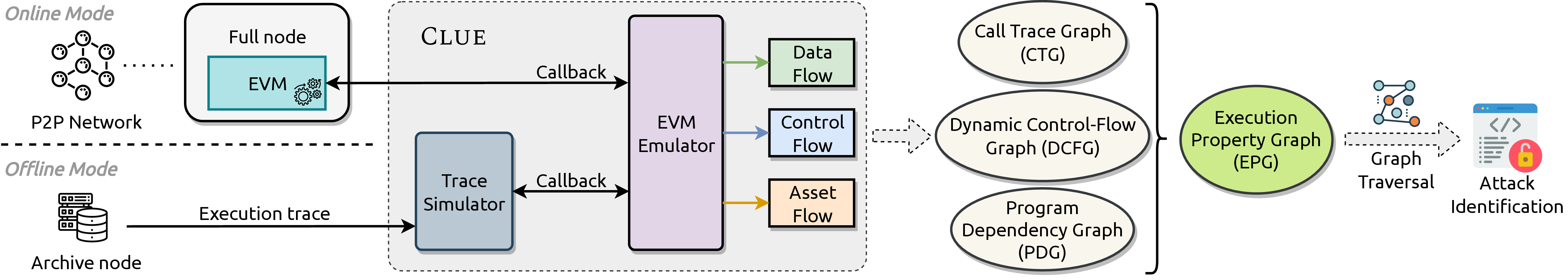
Contract Execution Representation Graphs
2023 | Kaihua Qin* · Zhe Ye* · Zhun Wang · Weilin Li · Liyi Zhou · Chao Zhang · Dawn Song · Arthur Gervais | https://arxiv.org/pdf/2305.14046.pdf
Identifying and mitigating vulnerabilities in smart contracts is crucial, especially considering the rapid growth and increasing complexity of DeFi platforms. To address the challenges associated with securing these contracts, we introduce a versatile dynamic analysis framework specifically designed for the EVM. This comprehensive framework focuses on tracking contract executions, capturing valuable runtime information, while introducing and employing the EPG to propose a unique graph traversal technique that swiftly detects potential smart contract attacks. Our approach showcases its efficacy with rapid average graph traversal time per transaction and high true positive rates. The successful identification of a zero-day vulnerability affecting Uniswap highlights the framework's potential to effectively uncover smart contract vulnerabilities in complex DeFi systems.


| Dataset | Attack | Non-Attack | |
|---|---|---|---|
| High-Gas | Regular | ||
| Size | 87 | 1,077 | 19,985 |
| Gas Cost | 3.33 ± 3.41M | 2.13 ± 1.38M | 0.24 ± 0.29M |
| Generic Rule | |||
| Traversal Time | 108 ± 136ms | 20 ± 21ms | 7 ± 3ms |
| TP (%) | 80 (91.95%) | - | - |
| FN (%) | 7 (8.05%) | - | - |
| TN (%) | - | 1075 (99.81%) | 19,984 (99.99%) |
| FP (%) | - | 2 (0.19%) | 1 (0.01%) |
| Refined Rule | |||
| Traversal Time | 0.32 ± 0.93s | 52 ± 109ms | 16 ± 347ms |
| TP (%) | 87 (100%) | - | - |
| FN (%) | 0 (0%) | - | - |
| TN (%) | - | 1,069 (99.26%) | 19,812 (99.08%) |
| FP (%) | - | 8 (0.74%) | 173 (0.87%) |
| Dataset | Attack | Non-Attack | |
|---|---|---|---|
| High-Gas | Regular | ||
| Size | 61 | 1,091 | 19,992 |
| Gas Cost | 0.22 ± 0.65M | 2.21 ± 1.53M | 0.24 ± 0.28M |
| Generic Rule | |||
| Traversal Time | 9 ± 18ms | 0.7 ± 8.6s | 13 ± 244ms |
| TP (%) | 38 (62.30%) | - | - |
| FN (%) | 23 (37.70%) | - | - |
| TN (%) | - | 942 (86.34%) | 14,850 (74.28%) |
| FP (%) | - | 149 (13.66%) | 5,142 (25.72%) |
| Refined Rule | |||
| Traversal Time | 48 ± 121ms | 8 ± 47s | 0.08 ± 3.07s |
| TP (%) | 46 (75.41%) | - | - |
| FN (%) | 15 (24.59%) | - | - |
| TN (%) | - | 1,074 (98.44%) | 18,879 (94.43%) |
| FP (%) | - | 17 (1.56%) | 1,113 (5.57%) |
| Dataset | Attack | Non-Attack | |
|---|---|---|---|
| High-Gas | Regular | ||
| Size | 54 | 1,075 | 19,989 |
| Gas Cost | 6.89 ± 3.37M | 2.14 ± 1.38M | 0.24 ± 0.26M |
| Generic Rule | |||
| Traversal Time | 32 ± 17ms | 7 ± 27ms | 2.2 ± 1.1ms |
| TP (%) | 53 (98.15%) | - | - |
| FN (%) | 1 (1.85%) | - | - |
| TN (%) | - | 322 (29.95%) | 18,410 (92.10%) |
| FP (%) | - | 753 (70.05%) | 1,579 (7.90%) |
| Refined Rule | |||
| Traversal Time | 47 ± 23ms | 10 ± 24ms | 2.4 ± 1.5ms |
| TP (%) | 51 (94.44%) | - | - |
| FN (%) | 3 (5.56%) | - | - |
| TN (%) | - | 1,059 (98.51%) | 19,886 (99.48%) |
| FP (%) | - | 16 (1.49%) | 103 (0.52%) |
Copyright ©2025 UC Regents | Email us at rdi@berkeley.edu.