
Motion as a Fingerprint
To date, the most comprehensive analysis of biometric identification is a 2003 study from the National Institutes of Standards and Technology (NIST), which analyzed dozens of commercially-available biometric sensors using real data from over 100,000 users. The results indicate that high-end fingerprint sensors could, at the time, identify users within a population of 10,000 with 90% accuracy. By contrast, our research shows that XR motion data can be used to identify at least 55,000 users, and likely more, with over 90% accuracy.
Learn More
Motion as DNA
In a second study, we surveyed 1,006 Beat Saber players to ask them a variety of questions about their background, biometrics, demographics, health information, behavioral patterns, and technical device specifications. Later, we trained a series of machine learning models to see which, if any, of these responses could be accurately inferred just by examining the motion patterns of these users. We found that everything from the country that a user is from to the clothes that they are wearing can be determined using features derived from their motions alone.
Learn More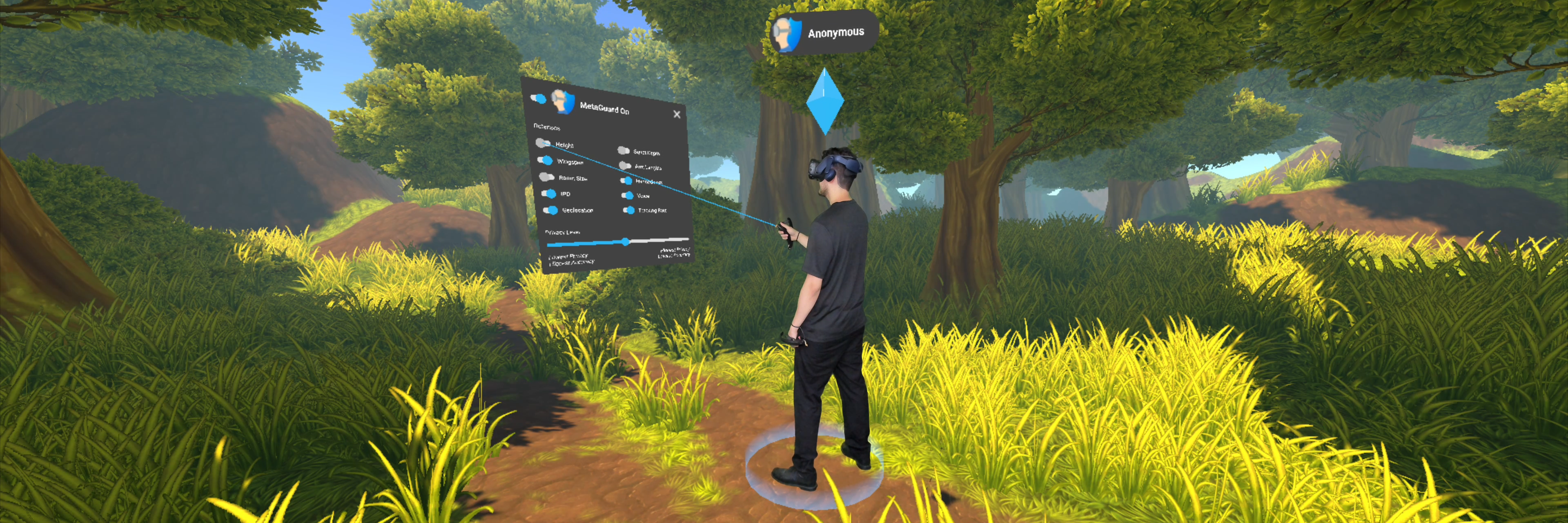
Safeguarding Motion
We developed "MetaGuard," an open-source plugin for the Unity game engine that we think of as a proof of concept for how to protect motion data in future XR experiences. Using MetaGuard, developers can select from three different "levels" of motion data protection, each of which applies a slightly more aggressive, yet reversible, transformation to the motion signals being sent over the internet. With MetaGuard Level 1, for example, 50,000 users can still be uniquely identified in our BOXRR dataset. At Level 3, this number drops to just 500.
Learn More